"– It’s easy to create reports that simplify collaboration across different parts of the organization."
M. Rowland
Systemair
vScope continuously discovers and maps every device in your network and cloud environment, consolidating them into a single on-premises asset repository.
Many cyberattacks exploit unknown or unmanaged devices and/or vulnerabilities in known systems. With a unified and continuously updated asset repository, you can ensure no blind spots remain in your IT environment.
Unlike niche security tools, vScope allows you to drill into asset details and their business context – such as owner, department, location and service – making it easier to understand their importance for your company’s security.
With a single source of truth, roles such as IT manager, technician, architect and system administrator can collaborate in one place to reduce risks, strengthen compliance and simplify the work of ensuring a secure operating environment.
"– It’s easy to create reports that simplify collaboration across different parts of the organization."
M. Rowland
Systemair
"– Instead of contacting our outsourcing partner for every update, we now get the information directly in vScope!"
J. Hallenbom
Green Landscaping
Bring everything together – from servers and clients to SaaS accounts and cloud assets – into a continuously updated asset repository.

Correlate software versions, patch status and configurations with ownership and business context. Detect shadow IT and vulnerable systems for more effective remediation.
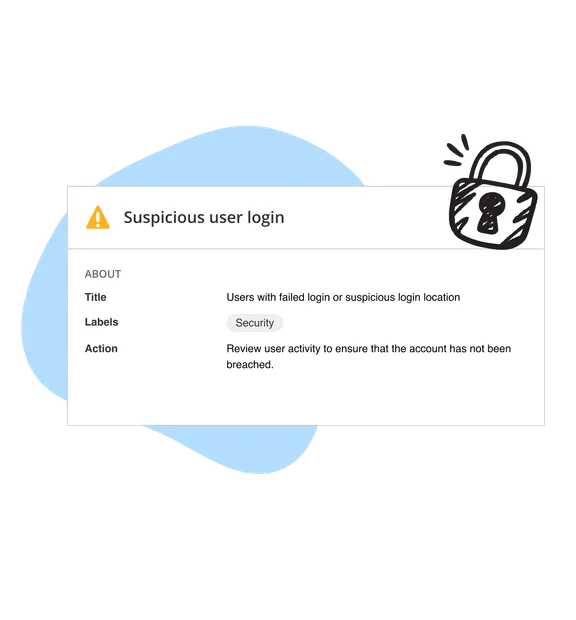
Simplify compliance with NIS2, ISO 27001, internal policies or other frameworks with a continuously updated asset repository. Predefined templates help you create audit reports and alerts within minutes.
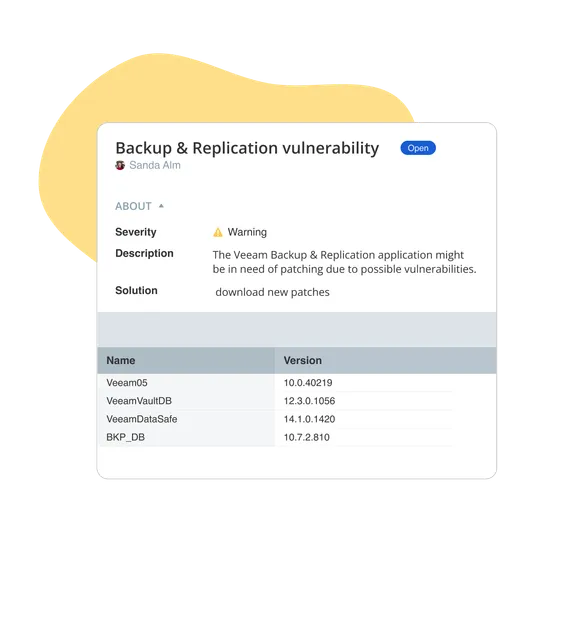
When something happens, instantly know which system is affected, where it is, and who is responsible. vScope provides context that reduces downtime and speeds up remediation.
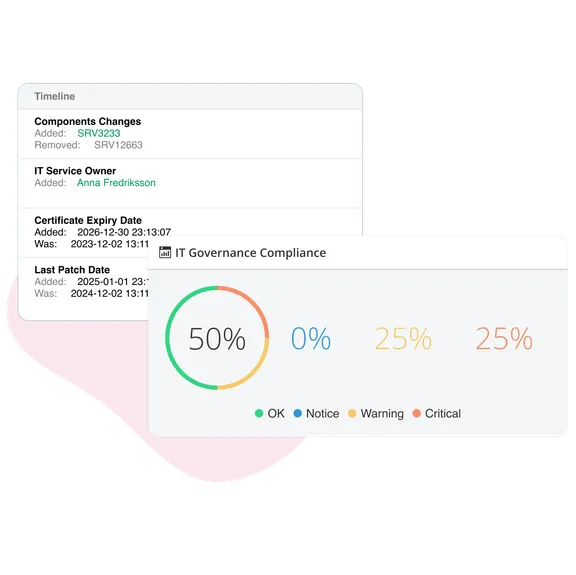
Comprehensive history makes audits and incident investigations manageable in hours instead of weeks.
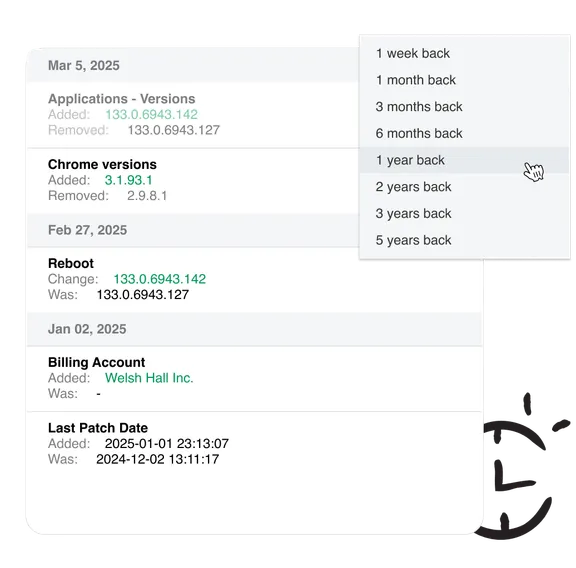
NIS2 requires organizations to have control over their IT assets. vScope automates discovery and reporting, giving you the complete visibility and traceability needed to meet NIS2 and ISO 27001.
Most breaches occur via unknown or unmanaged devices. With vScope, blind spots in your IT environment are eliminated, helping you prevent incidents and reduce risks.
Yes. vScope identifies unmanaged devices through network scanning – so you can detect and control shadow IT before it becomes a security problem.
Explore a complete checklist of the most important values in an IT inventory tool so you can feel confident in your buying decision.

Do you and your organization lack clear routines for communicating the value and costs of IT delivery? You’re not alone. Getting started doesn’t have to be difficult. Here are three practical ways to price IT and create a cost report that makes IT costs clear to the business.

Reduce manual pricing work and get more accurate IT billing in place faster using reusable, best-practice price list templates. Here is the latest feature of vScope Billing
One of the most requested features is now here. With Network Port Mapping for SNMP, IT teams can instantly see how devices are connected across the network, no more remoting into switches, outdated documentation, or guesswork. This update helps you troubleshoot faster, improve documentation, and strengthen overall network security.
Book a demo of vScope and see how you can meet NIS2 and reduce risks