
What is CMDB: A comprehensive guide to configuration management database
The Configuration Management Database (CMDB) is a crucial component of IT Service Management (ITSM). It serves as a central repository for storing and managing information about the various configuration items (CIs) within an organization's IT infrastructure. In this comprehensive guide, we will delve into the basics of CMDB, its key components, its role in ITSM, the process of implementing it, and the best practices for managing it effectively.
Understanding the Basics of a CMDB
Before we proceed further, let’s define what exactly a CMDB is and understand its significance in the context of IT. If you need more background about ITSM, I recommend you to check out the following blog post: Everything you need to know about ITSM (ITSM)
A Configuration Management Database (CMDB) is a database that contains information about all the Configuration Items (CIs) that are crucial to an organization’s IT infrastructure. It provides a detailed record of these CIs, including their attributes, relationships, and other relevant data.
A CMDB serves as a centralized repository for managing and tracking the configuration items within an organization. It acts as a single source of truth, ensuring that accurate and up-to-date information about the IT assets is readily available.
The importance of a CMDB cannot be overstated. It not only helps organizations keep track of their IT assets but also acts as a foundation for various IT Service Management (ITSM) processes such as incident management, change management, and problem management.
By maintaining a well-structured and well-maintained CMDB, organizations can gain valuable insights into their IT infrastructure. They can easily identify the dependencies and relationships between different configuration items, enabling them to understand the impact of any changes or incidents on the overall system.
Furthermore, a CMDB plays a crucial role in ensuring compliance with regulatory requirements and industry standards. It helps organizations demonstrate control over their IT assets and provides a clear audit trail for any changes made to the configuration items.
With the help of a CMDB, organizations can streamline their IT service delivery processes. They can quickly identify the root cause of incidents, track the progress of changes, and proactively manage potential problems. This not only improves the efficiency of IT operations but also enhances the overall quality of service provided to end-users.
In addition, a CMDB facilitates effective decision-making by providing accurate and reliable information. It enables IT managers to assess the impact of proposed changes, evaluate the risks associated with them, and make informed decisions based on data-driven insights.
Overall, a well-maintained CMDB is an invaluable asset for any organization. It empowers IT teams to effectively manage their IT infrastructure, optimize service delivery, and ensure the stability and reliability of their systems.
Key Components of a CMDB
A Configuration Management Database (CMDB) is a critical tool for effective configuration management within an organization. It consists of various key components that work together seamlessly to ensure accurate and up-to-date information about the organization’s configuration items. Let’s explore these components in detail.
Configuration Items (CIs)
At the heart of a CMDB are the Configuration Items (CIs). These CIs serve as the building blocks that represent the various elements within an organization’s infrastructure. They can include a wide range of components such as hardware devices, software applications, databases, network components, and more. Each CI is assigned a unique identifier, enabling easy identification and tracking within the CMDB.
By including a comprehensive range of CIs, organizations can gain a holistic view of their entire infrastructure, allowing them to effectively manage and control their configuration items. This, in turn, ensures that any changes or updates made to these items are accurately recorded and tracked within the CMDB.
Attributes and Relationships
Within a CMDB, each CI is associated with a set of attributes that provide additional information about the item. These attributes can include details such as the CI’s name, type, version, owner, location, and other relevant information. By capturing and maintaining these attributes, organizations can have a comprehensive understanding of their configuration items, facilitating effective decision-making and troubleshooting.
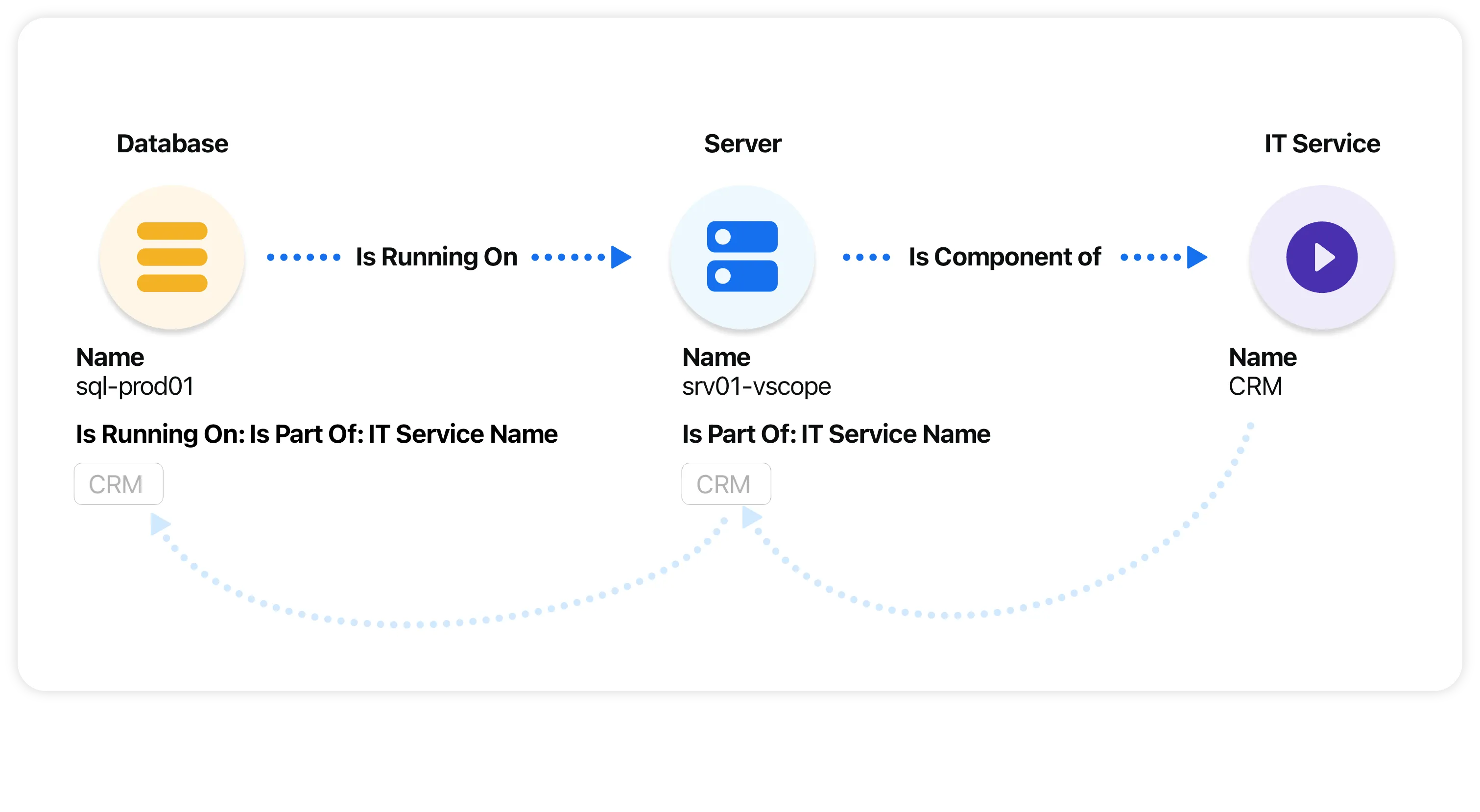
In addition to attributes, relationships play a crucial role in a CMDB. Relationships define the connections and dependencies between different CIs. By establishing and documenting these relationships, organizations can gain insights into how changes to one CI can impact others. This knowledge is invaluable when planning changes or troubleshooting issues within the infrastructure.
For example, if a software application CI is connected to a database CI, any changes made to the database configuration might have implications for the application’s functionality. By understanding this relationship, organizations can proactively plan and mitigate any potential risks or disruptions.
Furthermore, relationships in a CMDB can extend beyond direct connections between CIs. They can also include relationships with other entities such as users, departments, or locations. This broader perspective allows organizations to better understand the impact of configuration changes on different aspects of their operations.
In conclusion, a CMDB consists of various key components that work together harmoniously to ensure effective configuration management. Configuration Items (CIs) serve as the fundamental building blocks, while attributes and relationships provide the necessary context and connections. By leveraging these components, organizations can achieve better control, visibility, and understanding of their infrastructure, leading to improved decision-making and operational efficiency.
The Role of CMDB in IT Service Management (ITSM)
Now that we have a good understanding of the basics, let’s explore how a Configuration Management Database (CMDB) plays a crucial role in various IT Service Management (ITSM) processes.
A CMDB is a centralized repository that stores information about Configuration Items (CIs) within an organization’s IT infrastructure. It provides a comprehensive view of the relationships and dependencies between these CIs, enabling organizations to effectively manage their IT services.
Incident Management and CMDB
In incident management, a CMDB helps IT teams quickly identify the affected CIs and their relationships, leading to faster resolution of incidents. When an incident occurs, the CMDB provides valuable insights into the impacted CIs, their associated services, and the dependencies between them.
For example, let’s say a critical server goes down, causing a service disruption. With a CMDB in place, the IT team can easily identify the server, its dependencies (such as network switches and storage devices), and the services that rely on it. This information allows them to prioritize the incident, allocate resources effectively, and restore services in a timely manner.
Furthermore, a CMDB enables organizations to analyze the impact of incidents on their services. By correlating incident data with CMDB information, IT teams can identify recurring issues, spot trends, and take proactive measures to prevent future incidents.
Change Management and CMDB
During change management, a CMDB provides insights into the current state of the IT environment, allowing organizations to assess the potential impact of changes and plan them accordingly. It ensures that changes are implemented smoothly and without causing unintended consequences.
When a change request is submitted, the CMDB plays a crucial role in evaluating the impact of the proposed change. It provides a comprehensive view of the affected CIs, their relationships, and the services they support. This information helps organizations assess the risks associated with the change, determine the necessary approvals and resources, and develop an effective implementation plan.
For example, let’s consider a scenario where a software upgrade is planned for a critical application. By leveraging the CMDB, organizations can identify all the CIs that are associated with the application, such as servers, databases, and network components. They can then assess the potential impact of the upgrade on these CIs and plan accordingly, ensuring that the change is implemented smoothly and without causing disruptions to the services.
In addition, a CMDB provides organizations with a historical record of changes, allowing them to track and audit the modifications made to their IT infrastructure. This information is valuable for compliance purposes and helps organizations maintain a reliable and secure IT environment.
Implementing a CMDB
Implementing a CMDB requires careful planning and execution. Let’s explore the necessary steps to successfully implement a CMDB.
Steps to Implement a CMDB
The implementation process typically involves identifying the scope and objectives of the CMDB, defining the CI taxonomy, gathering and importing the initial CI data, setting up the necessary infrastructure, configuring the CMDB software, and performing rigorous testing before going live.
Common Challenges and Solutions
While implementing a CMDB, organizations often face challenges such as data inconsistencies, lack of collaboration, and resistance to change. Addressing these challenges requires proper data cleansing, encouraging cross-functional collaboration, and educating stakeholders about the benefits of the CMDB.
Best Practices for CMDB Management
Effectively managing a CMDB is essential to maintain its accuracy and relevance over time. Here are some best practices to ensure successful CMDB management.
Regular Auditing and Cleanup
Regularly auditing the CMDB ensures that the information stored within it is accurate, up-to-date, and reflects the current state of the IT environment. Cleanup activities involve identifying and removing duplicate or obsolete records, resolving data inconsistencies, and performing data normalization.
Integrating CMDB with Other ITSM Tools
Integrating the CMDB with other ITSM tools such as incident management, change management, and service catalog systems enhances its functionality and enables organizations to have a holistic view of their IT services. This integration promotes data consistency, streamlines processes, and improves overall service delivery.
In Conclusion
In conclusion, the Configuration Management Database (CMDB) is a fundamental component of ITSM that helps organizations effectively manage their IT assets. Understanding the basics of CMDB, its key components, its role in ITSM processes, implementing it successfully, and following best practices for CMDB management are essential for organizations to achieve optimal service delivery and maximize the value of their IT infrastructure.
Related blog posts
All posts
Create a Great Cost Report: Three Ways to Price Your IT Environment
Do you and your organization lack clear routines for communicating the value and costs of IT delivery? You’re not alone. Getting started doesn’t have to be difficult. Here are three practical ways to price IT and create a cost report that makes IT costs clear to the business.

How to rightsize databases with vScope
Rightsizing your IT environment is a powerful way to optimize costs. Preparing for database resource migration offers a great chance to phase out unused elements and save on operational and licensing budgets. In this article, we will learn how to investigate database usage, identify unused resources, and significantly lower costs for both migration and future operations.

Full Control Over Users and Issues in Jira with vScope
We're excited to announce the initial integration with Atlassian Jira, the leading platform for project and issue tracking. This enhancement will provide you with an improved overview of users, activity, and issues directly within vScope, simplifying the process of tracking license utilization, identifying opportunities for cost efficiency, and connecting issues to relevant services.

Securing Your Windows Data Center: Best Practices for IT Discovery Read Accounts
Gaining comprehensive visibility into your IT environment is crucial for accurate asset inventory, documentation, and effective security audits. However, granting overly broad access and permissions for user accounts can introduce significant security vulnerabilities, making the careful management of user account access a critical concern.

Getting Started with IT Governance in vScope
IT governance can be challenging when managing complex IT assets, documentation, and compliance. vScope simplifies this process with vScope Governance, a features that deliver complete visibility and streamlined collaboration across your network. In this post I will share three tips to get started and get the most out of IT governance in vScope.

The Ultimate Guide to IT Asset Inventory: Best Practices and Tools
In the ever-evolving world of technology, managing and maintaining IT assets is crucial for the smooth functioning of any organization. From hardware devices and software licenses to network equipment and digital resources, IT asset inventory plays a significant role in ensuring optimal performance and cost-effective operations.

Everything you need to know about ITSM
How can IT organizations better align their operations to support the main business objectives? How can technology facilitate more efficient workflows in the company as a whole and how can IT staff continuously improve its operations to deliver better IT services? These questions are some of the reasons why companies are investing in, implementing, and developing ITSM processes.

3 steps to reduce your IT costs
As IT is becoming an integral part of organizations the costs of IT are increasing. Many businesses are therefore looking for ways to reduce their IT costs. Here we present 3 tips to reduce your IT costs!

3 common challenges with ITAM
IT asset management (ITAM) is an incredibly efficient way to keep track of your IT assets – if it is executed correctly. In this article, we explore three common challenges associated with ITAM and how to solve them.